This is an alert to inform all Microsoft Office users of a new zero-day attack that installs malware onto a fully patched system running Microsoft Operating System via an Office vulnerability. We recommend refraining from sending or opening any Word documents via email. This type of phishing emails can come in different formats including Resumes, Invoices, Tracking numbers, demand notice, etc.
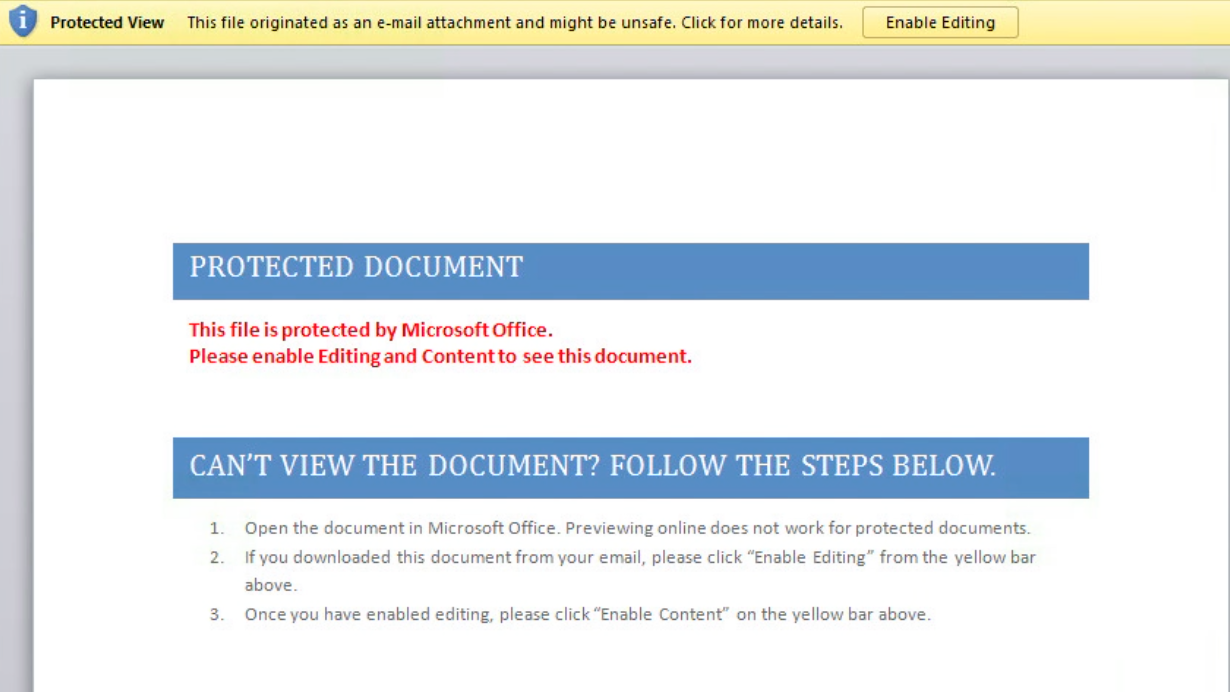
Microsoft Office has a feature called “Protected View” that is enabled by default; however, you should double check your settings to make sure that this feature is turned on. If you open a Word document and see this pop-up, it’s a pretty good indicator that something is wrong.
In addition to being highly suspicious of any Word document that arrives in an email, there are a few other things we’d recommend that you consider:
- Consider sharing documents through your internal network file server instead of email.
- Do not open or download any suspicious Word files that arrive in an e-mail, even if you know the sender until Microsoft releases a patch.
- Since the attack does not work when a malicious document is viewed in Office Protected View feature, users are advised to enable this feature to view any Office documents.
- Disabling Macros does not offer any protection, but yet users are advised to do so in an attempt to protect themselves against other attacks.
- Always beware of phishing emails, spams, and clicking the malicious attachment.
The vulnerability is bypassing most mitigations, and we will push the Microsoft patch as soon as it is available.
